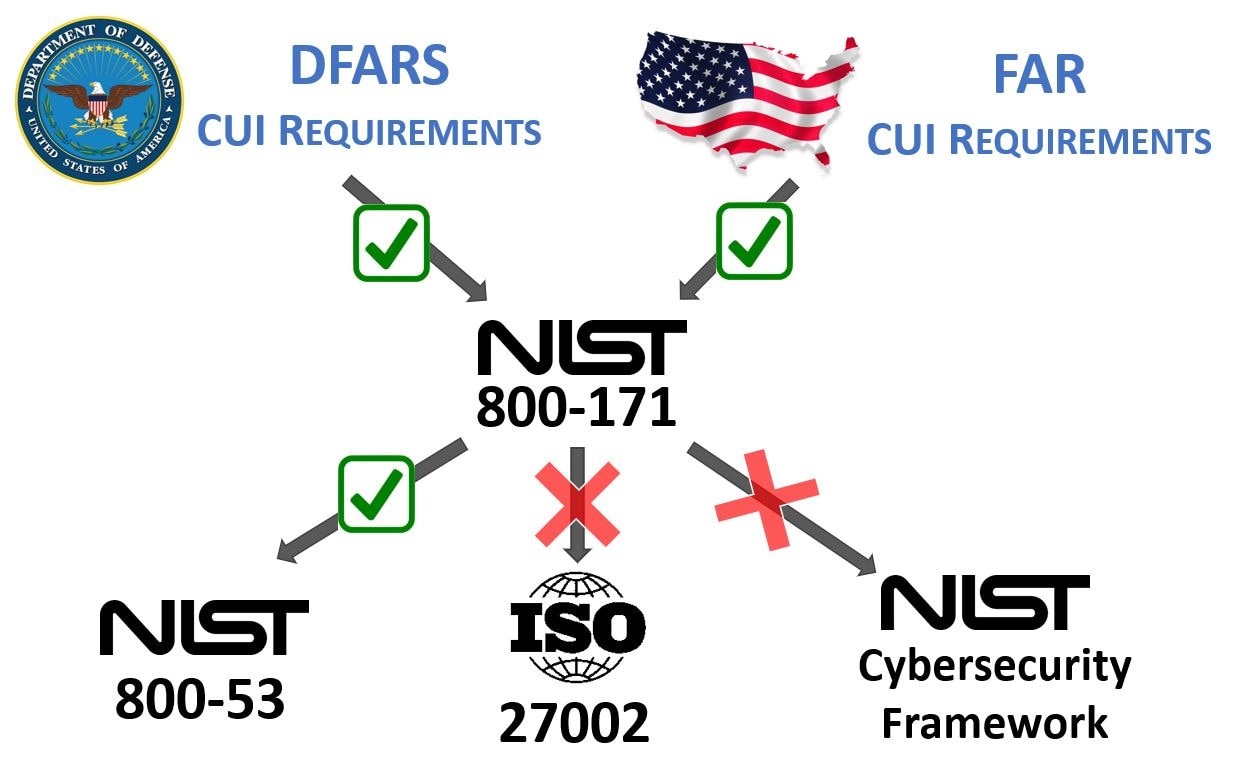
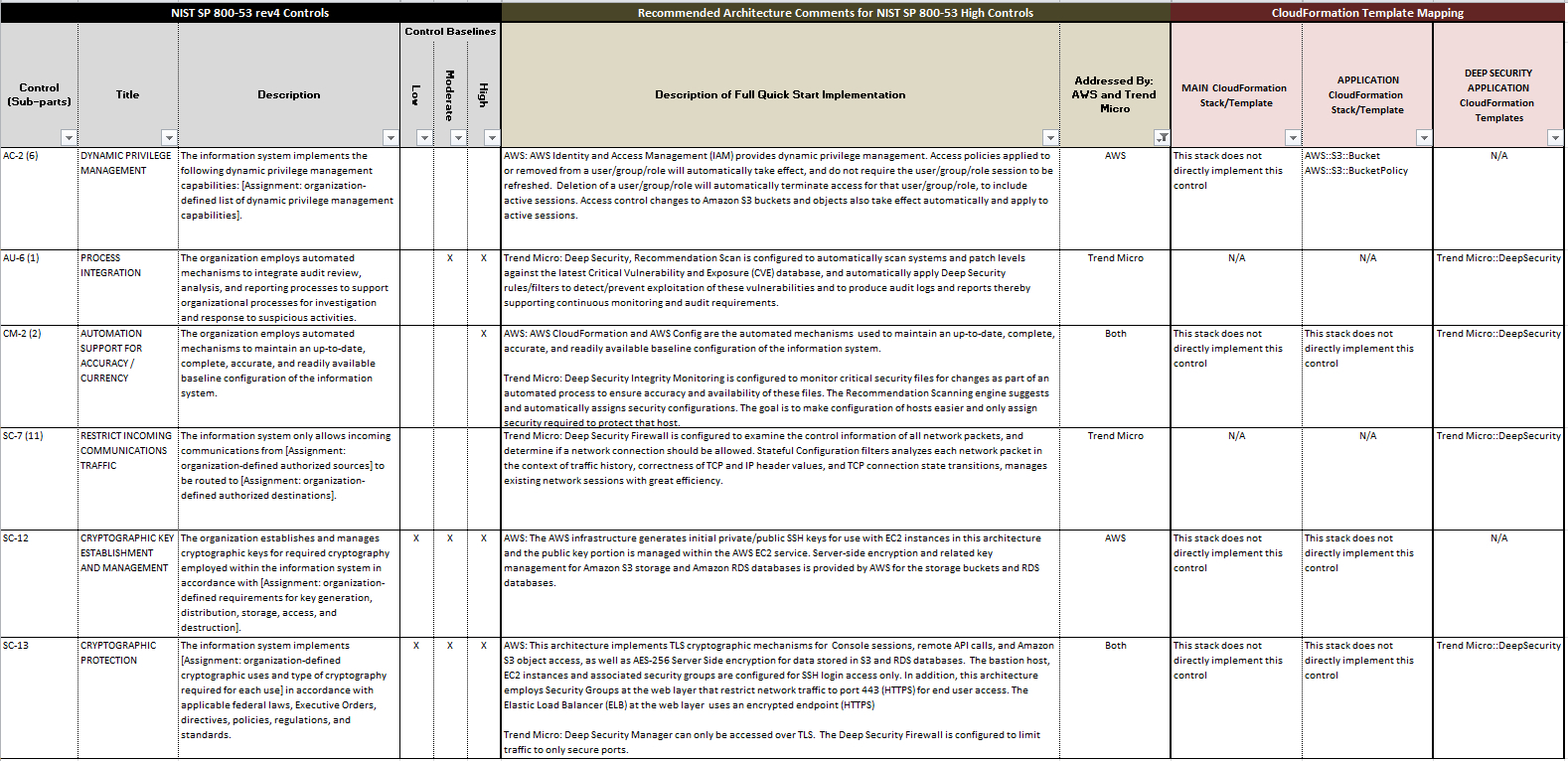
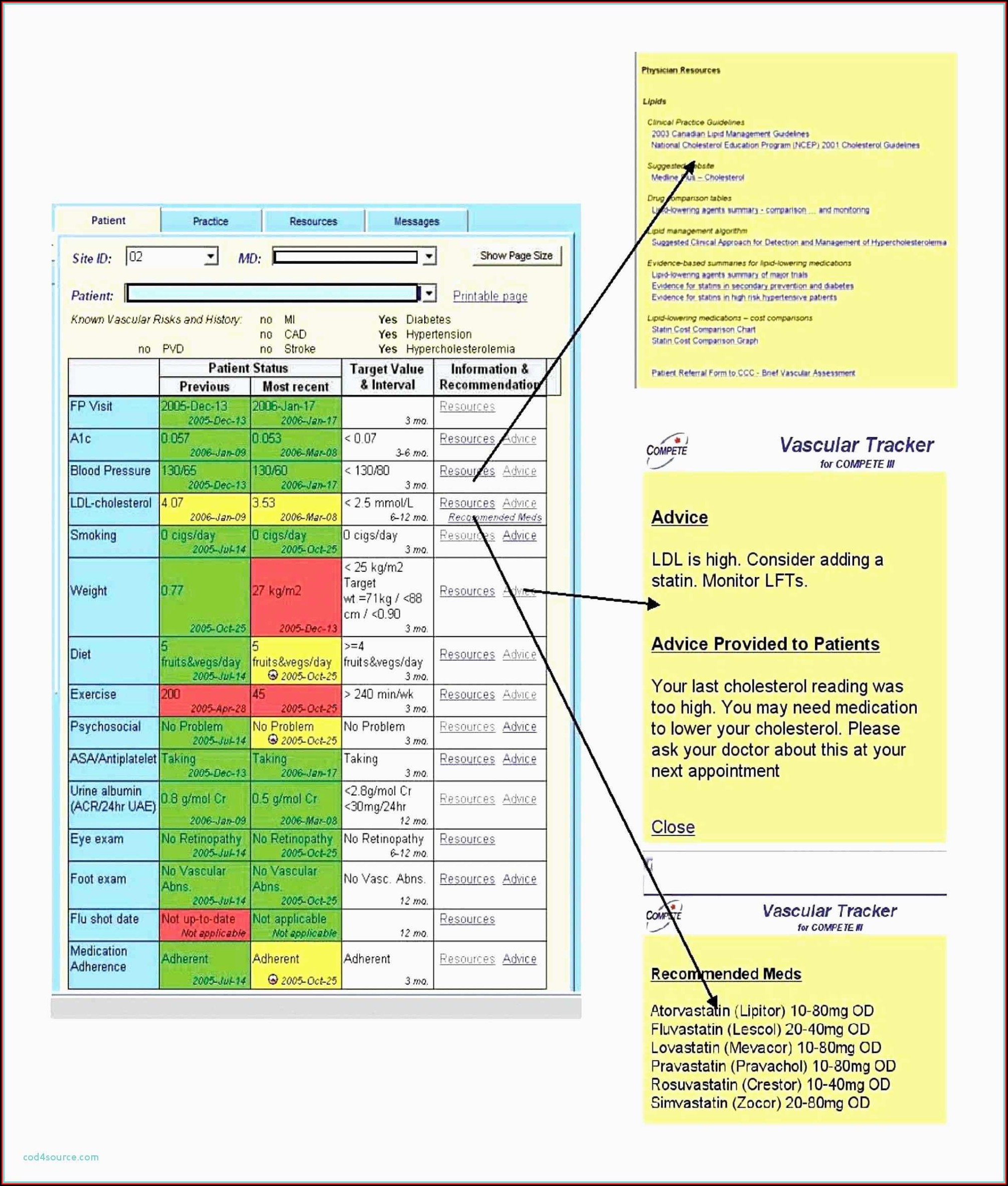
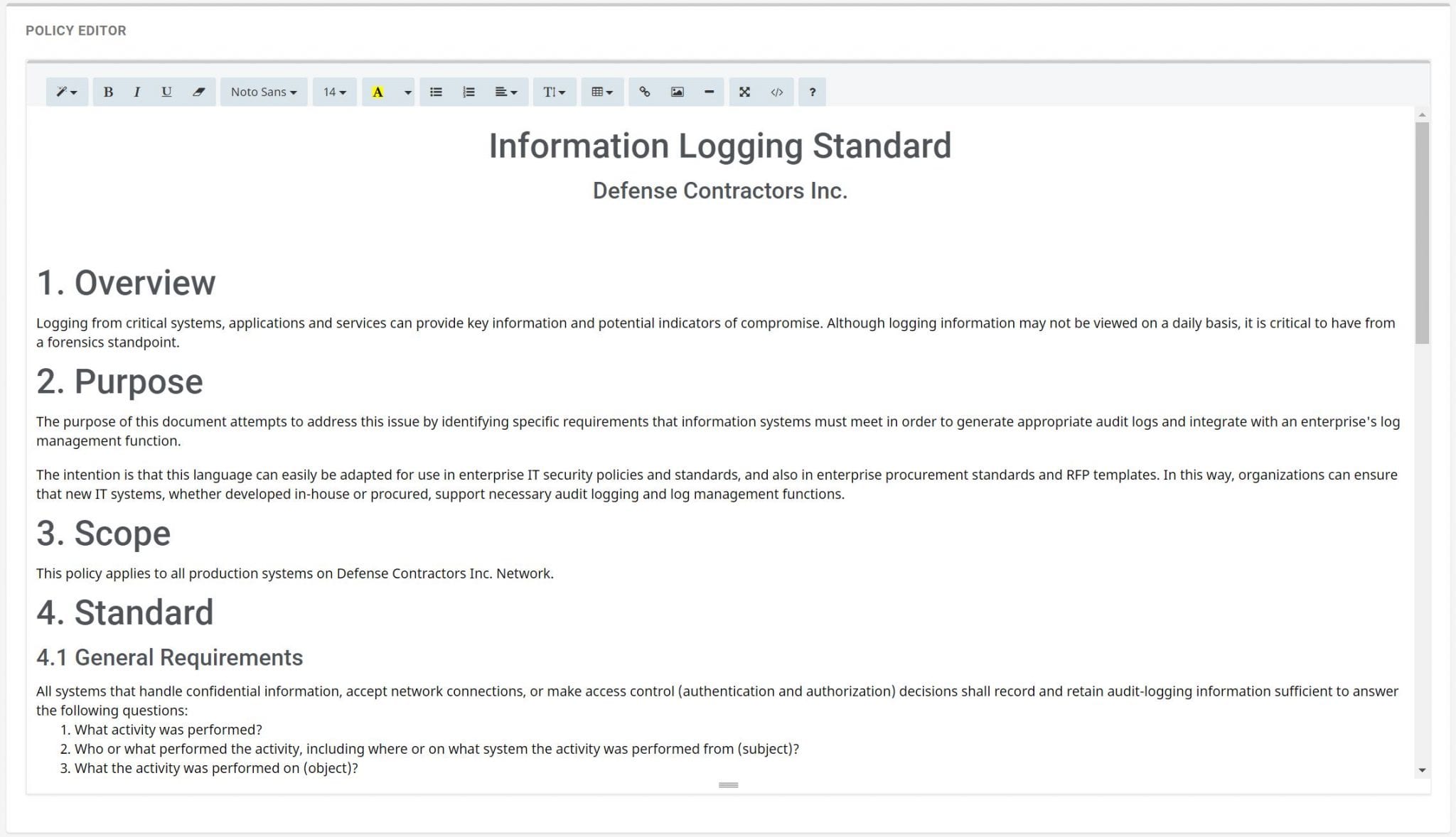
Nist 800 171 Policy Templates Free - Web information security policy templates | sans institute. We use the list of countries in itar part 126.1. The itar policy will help. Control catalog spreadsheet the entire security and privacy control catalog in spreadsheet format. Ad download your security policy and access all our 2,000+ templates. Web welcome to the cmmc policy creator! Web our itar template uses the usml (u.s. The templates can be customized and used as an outline of an organizational. Web the policy templates are provided courtesy of the state of new york and the state of california. We have mastered the art of automating cybersecurity maturity model certification (cmmc) information security policy creation.
Nist 800 171 Policy Templates Free Resume Gallery
If there are any discrepancies noted in the content between the. The templates can be customized and used as an outline of an organizational. We use the list of countries in itar part 126.1. Web information security policy templates | sans institute. Ad make your free online customized information security policy.
Nist 800 171 Spreadsheet regarding Sheet Nistreadsheet Compliance
The itar policy will help. Business plans, contracts, hr, finance, marketing, administration. We use the list of countries in itar part 126.1. Ad download your security policy and access all our 2,000+ templates. Your trusted support for all things business related, get help from attorneys today.
Rmf Controls Spreadsheet Spreadsheet Downloa rmf controls spreadsheet.
Web information security policy templates | sans institute. Web summary of supplemental files: Included speciality, control output the after: The templates can be customized and used as an outline of an organizational. Web nist cui poam template (.docx).
Nist 800 171 Access Control Policy Template Template 1 Resume
Web linkages and review off templates available for the cmmc assessment process. We use the list of countries in itar part 126.1. We have mastered the art of automating cybersecurity maturity model certification (cmmc) information security policy creation. Web cmmc requires policies, documented practices or procedures, and plans that cover every control. The itar policy will help.
Nist 800 171 Template Template 1 Resume Examples edV14nrYq6
Web information security policy templates | sans institute. Web summary of supplemental files: Munitions list) for controlled arms and weapons in itar part 121. Policy templates, tracking types, and professional evidence collection tools. Web cmmc requires policies, documented practices or procedures, and plans that cover every control.
Nist Policy Templates Master of Documents
We use the list of countries in itar part 126.1. Web the policy templates are provided courtesy of the state of new york and the state of california. Web information security policy templates | sans institute. We have mastered the art of automating cybersecurity maturity model certification (cmmc) information security policy creation. Business plans, contracts, hr, finance, marketing, administration.
Nist 800 53 Spreadsheet For Templates Nist 80053 Controls Spreadsheet
Web the policy templates are provided courtesy of the state of new york and the state of california. Web information security policy templates | sans institute. Registration information will be posted next week on the protecting cui. Munitions list) for controlled arms and weapons in itar part 121. Agree with both lepats links below as good resources.
Data Classification Policy Template Nist
The itar policy will help. Web linkages and review off templates available for the cmmc assessment process. Web nist cui poam template (.docx). Included speciality, control output the after: Your trusted support for all things business related, get help from attorneys today.
Nist 800 171 Poa&m Template Template 1 Resume Examples 05KAgna8wP
Ad discover how to use splunk meet compliance mandates, save time, and reduce costs. Web our itar template uses the usml (u.s. Policy templates, tracking types, and professional evidence collection tools. Web information security policy templates | sans institute. The templates can be customized and used as an outline of an organizational.
NIST 800171 "Easy Button" Compliance for Small & Medium Businesses
Registration information will be posted next week on the protecting cui. Learn about the future of cybersecurity in light of these new compliance mandates Web linkages and review off templates available for the cmmc assessment process. Web cmmc requires policies, documented practices or procedures, and plans that cover every control. If there are any discrepancies noted in the content between.
If there are any discrepancies noted in the content between the. Ad download your security policy and access all our 2,000+ templates. Registration information will be posted next week on the protecting cui. Web nist cui poam template (.docx). Learn about the future of cybersecurity in light of these new compliance mandates Web 20 hours agothe national institute of standards and technology (nist) requested public input on the research cybersecurity resources it might develop for colleges and. Web the policy templates are provided courtesy of the state of new york and the state of california. The templates can be customized and used as an outline of an organizational. Ad make your free online customized information security policy. Included speciality, control output the after: We have mastered the art of automating cybersecurity maturity model certification (cmmc) information security policy creation. Control catalog spreadsheet the entire security and privacy control catalog in spreadsheet format. We use the list of countries in itar part 126.1. Web linkages and review off templates available for the cmmc assessment process. Business plans, contracts, hr, finance, marketing, administration. Munitions list) for controlled arms and weapons in itar part 121. Web cmmc requires policies, documented practices or procedures, and plans that cover every control. The itar policy will help. Web summary of supplemental files: Web welcome to the cmmc policy creator!
Business Plans, Contracts, Hr, Finance, Marketing, Administration.
Ad download your security policy and access all our 2,000+ templates. Web welcome to the cmmc policy creator! Web our itar template uses the usml (u.s. Learn about the future of cybersecurity in light of these new compliance mandates
Web Linkages And Review Off Templates Available For The Cmmc Assessment Process.
We use the list of countries in itar part 126.1. Policy templates, tracking types, and professional evidence collection tools. Included speciality, control output the after: Ad discover how to use splunk meet compliance mandates, save time, and reduce costs.
Web Summary Of Supplemental Files:
Your trusted support for all things business related, get help from attorneys today. The templates can be customized and used as an outline of an organizational. We have mastered the art of automating cybersecurity maturity model certification (cmmc) information security policy creation. Munitions list) for controlled arms and weapons in itar part 121.
Web Nist Cui Poam Template (.Docx).
Web information security policy templates | sans institute. Control catalog spreadsheet the entire security and privacy control catalog in spreadsheet format. Web cmmc requires policies, documented practices or procedures, and plans that cover every control. Ad make your free online customized information security policy.